Internet of Things: Security and Privacy Concerns
- Physical devices and sensors
Physical devices and sensors are able to gather and sense first-hand and multidimensional information, and evidence of the objective condition of an event autonomously without human intervention. In addition, when devices function to capture information with embedded intelligence, devices can act and react. Environment context will then be modified and the devices will respond differently. As such, this circular process will be repeated continuously.
- Connection and infrastructure
Connection and infrastructure, such as cloud, security, storage, security, privacy and processing, facilitate continuous, real-time data and information flow and feedback loops.
- Analytics and applications
Analytics and applications transform sensorgenerated information to a new and key source of knowledge for action-taking. They enable users to leverage the large amount of data gather, converge information for further analysis provides actionable insight for the enterprise for productivity enhancement, offer unique solutions, and enhance life experience.

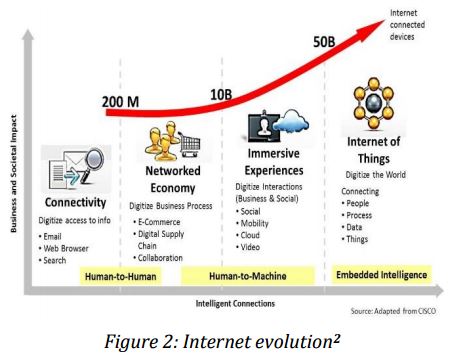
with each other without human intervention.

- Big Data
With the variety and enormity of data and information collected by the sensors, Big Data technologies will be the cornerstone in extracting meanings and insights of this exponentially increased data, which will enrich the user experiences and enable new business processes and models.
- Cloud
Cloud serves as delivery platform of information and functionality to users. Cloud allows information and knowledge to be accessed and delivered to anyone, anytime and anywhere.
- Social media
Social media is transforming interaction and communication modes between individuals in new and unexpected ways. Information will be sourced from physical movement and interactions happening in the Web 2.0. Interconnected societal promote engagements, share information, collaborate and innovate.
- Mobile devices/things
Mobile devices/things are the platforms of social communication and network in both personal and work spheres. With the diminishing cost of device that drives the revolution of sensors and connected things, data capturing is no longer restricted by locations and a single dimension. Data collection process escalated both in speed and scale and multidimensional variables can be captured simultaneously within the same environment.
Several challenges need to be addressed in order to encourage higher growth rate of IoT and subsequently provide opportunities for Universities and the industry to capture new competencies and capacities Several thematic challenges have been identified from various stakeholders of the IoT ecosystem.
- Infrastructure
Infrastructure is the catalyst to reach an interoperable, trustable, mobile, distributed, valuable, and powerful enabler for emerging applications such as Smarter Cities, Smart Grid, Smart Building, Smart Home, Intelligent Transport Systems, and ubiquitous healthcare, to name a few. The massiveness of sensors and smart things to be connected to the Internet will pressure the adoption of IPv6, which is a technology considered most suitable for IoT, as it offers scalability, flexibility, tested, extended, ubiquitous, open, and end-to-end connectivity11.
- Data & Information
The tremendous volume of data that pours in from devices presents a huge challenge for service providers in the IoT ecosystem. Big Data solutions will be instrumental in overcoming this challenge by giving IoT service providers the capacity to analyse data, and discover relevant trends and patterns.
Issues including privacy related to personal data, and data sharing12 will emerge, denoting the importance of trust in establishing the ecosystem that supports consumers in donating their data for public good.
- Security & Privacy
Connected devices can communicate with consumers, transmit data back to service providers, and compile data for third parties such as researchers, health care providers, or even other consumers. The supply chain of information in the era of IoT brings new challenges for regulators, enterprises and consumers. Findings from TRUSTe Internet of Things Privacy Index reveal that UK consumers’ comfort level varies widely depending on responsibility, ownership and usage of collected personal data13.
- Ecosystem
The IoT revolution is already under way. ‘Things’ (for example, everyday objects, environments, vehicles and clothing) will have more and more information associated with them, and are beginning to sense, communicate, and produce new information, to become an integral part of the Internet. Added value services using the IoT could reach £200bn a year worldwide14, with new business models, applications and services developing across different sectors of the economy. These will also stimulate innovation and growth in areas such as components, devices, wireless connectivity, system integration and decisionsupport tools.
- Threat Posed by Compromised Devices
Since many devices contain inherent values by their design and nature of functions, a connected device presents a potential target to be exploited by an attacker. A connected security camera could expose personal information, such as user’s location when compromised. As devices will be trusted with the ability to control and manage things, they are also capable of impacting things. This could be something as simple as controlling the lights in house or business premises, or something as malicious as controlling an automobile or medical device in a way that could cause physical harm.
- Threat over Communication Link
Threat over communication link involves monitoring and intercepting messages during a communication session. Due to the volume and sensitivity of data traversing the IoT eco-systems, attacks of targeting communication link are especially dangerous, as messages and data might be intercepted, captured, or manipulated while in transit. For example, an attacker could track the energy usage to learn of the downtime or uptime of a system (for example business premises)to plan an attack on the entire core smart cities command & control systems; the other attacker could manipulate the data transmitted to the utility company and alter the information. Successful breaches, such as these examples, may compromise the trust in the information and data transmitted across IoT infrastructure.
|
Manipulation of Connected Cars
Security researcher Chris Valasek and Charlie Miller15 in their research discovered the vulnerability of connected cars. The duo experimented a Toyota Prius and a Ford Escape and plugged the exploits tools into the vehicle’s diagnostic port. This allowed the team to manipulate the cars headlights, steering, and breaking systems.
Threats to Medical Devices
Security researchers Scott Erven16 and his research team released the results of a two-year studies on the vulnerability of medical devices. The results demonstrated the possibility of remote manipulation of medical devices, including those that controlled the dosage levels for drug infusion pumps and connected defibrillators. The results exposed the severity of threats posed to the security of patients and medical system.
|

Threats against IoT device manufacturer and cloud service providers have the potential to compromise the entire IoT ecosystem, as manufacturer and IoT cloud are entrusted with hosting trillions amount of data, some of which is highly sensitive by nature. This data is important because it represents an analytics, which is a core, strategic asset, it is a significant amount of competitive information in the eyes of underground APT group if exposed. If the Master is compromised, this would give the attacker opportunity to manipulate many devices at once, some of which may have already been deployed in the field. For example, if a provider who issues frequent firmware / software have the mechanism compromised, malicious code could be introduced to the devices.





- Data-at-Rest Protection
Encrypting data is all about providing scalable, costeffective storage, and fast processing of large data sets that facilitates the availability and usage of the said data. Typically, this data will be stored in clusters spread across hundreds to thousands of data nodes. This data is largely unprotected, making each data node a potential entry point for a rogue insider or malicious threat, and leaves sensitive data in clear view should an unauthorised user or service gain access. This presents a tremendous, and potentially costly, risk for organizations.
To overcome this challenge, organizations need to be able to lock down sensitive data at rest in big data clusters without impacting performance. Doing so requires transparent and automated file-systemlevel encryption that is capable of protecting sensitive data at rest on these distributed nodes.
- Data-in-Motion Protection
Encrypting communication as data moves through the IoT ecosystem presents a unique challenge. As data moves from one location to another, it is highly vulnerable to attacks such as fibre tapping. An attacker can attach an evanescent fibre coupling device to the cable without detection. This allows the attacker to record all activity that runs across the network, and data is captured and stolen without the owner’s knowledge. Worst, this type of attack can also be used to change data, and has the potential to override the controls on the entire system.
IoT communication over public networks will need to be secured in much the same way we protect other communications via the Internet. Transport layer security (TLS)20 is a good example of encryption protocols that could be used for this purpose. Encryption is also needed at the back-end infrastructure level of manufacturers, cloud service providers, and IoT solution providers.
- TELEFÓNICA I+D: Internet of Things + Internet of Services (2008)
- http://www.internetlivestats.com/internet-users (visit 2015)
- Gartner Says “the Internet of Things Will Transform the Data Center” (2014)
- Pranabesh Nath, “Internet of Things & Connected Industries: Driving New Applications”, Frost & Sullivan, 6th Annual Customer Interaction Malaysia (2014)
- Charles Reed Anderson, “The internet of Things: The possibilities are endless, but how will we get there?”; IDC APeJ Internet of Things Web Conference (2014)
- Bradley, J., Barbier, J., & Handler, D. Embracing the Internet of Everything to capture your share of $14.4 trillion. Cisco.(2013)
- Ericson, “More than 50 billion connected devices”(2011)
- GSMA, “Mobile Economy 2014”
- TNW News, “Report: Asia-Pacific is home to 1.7 billion mobile subscribers, half of the world’s total” (2014)
- UMTS Forum (Jan 2011), “Mobile traffic forecasts 2010-2020”; (retrieved on 14 July 2014)
- Jara, A.J., Ladid, L. and Skarmeta. A. “The Internet of Everything through IPv6:An Analysis of Challenges, Solutions and Opportunities”. Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications, volume: 4, number: 3, pp. 97-118. (2013)
- Robert Wood Johnson Foundation, “Personal Data for the Public Good” (2014)
- Davies, J. “Internet of Things crisis? Privacy issues could be barrier to smart-device take-up, says Ipsos Mori report”(2014)
- Technology Strategy Board. “Internet of Things convergence: Competition for funding of preparatory studies” (2011).
- Forbes, “Hackers Reveal Nasty New Car Attacks--With Me Behind The Wheel (Video)” (2013)
- WIRED, “It’s Insanely Easy To Hack Hospital Equipment” (2014)
- ICS-CERT, “Internet Accessible Control Systems At Risk” (2014)
- MIMOS, “National IoT Strategic Initiative Blueprint” (2015)
- Wikipedia, “Public Key Cryptography” (Visit 2015)
- http://postscapes.com/internet-of-things-protocols (visit 2015)
- Tim Sisson, “What is SSL and why is it important? ” http://www.inmotionhosting.com/support/website/ssl/what-is-ssl-and-why-is-it-important (2013)
- Wikipedia, “Elliptic Curve Cryptography” https://en.wikipedia.org/wiki/Elliptic_curve_cryptography (visit 2015)